| |
| |
 |
|
| |
|
|
 |
May 2006
|
 |
| |
|
|
|
| |
In this issue:
1. Guest Spot: Securing Lawson Self-Service
2. CUE 06: Was "9 on Your Mind"?
3. Worthwhile Reading
4. Lawson Tips & Tricks
The LawsonGuru Letter is a free periodic newsletter providing provocative commentary on issues important to the Lawson Software community. The LawsonGuru Letter is published by—and is solely the opinion of—John Henley of Decision Analytics.
Visit Decision Analytics at https://www.danalytics.com. For subscription information, see the bottom of this message. The LawsonGuru Letter is not affiliated with Lawson Software.
Alex Tsekhansky from Analysts International is back again this month to take the Guest Spot. Security is always a popular topic when it comes to Lawson, and Alex shares some important insights on securing IOS and Lawson's SEA products. As always, I'm extremely grateful to our Guest Spot contributors! Ready to take your turn? Drop me a line at letter-editor@lawsonguru.com.
|
|
|
| |
|
|
|
| |
1. Guest Spot: Securing Lawson Self-Service |
 |
|
| |
(by Alex Tsekhansky, Analysts International)
|
|
|
| |
|
|
|
| |
Self-service products simplify access and data entry to several Lawson modules, such as Human Resources and Procurement suites. In a current version those products can sustain thousands of concurrent users with the right hardware and configuration. More and more companies enable access to those products for large user communities, and some companies enable access to self-service from the Internet. In this article we will discuss securing Lawson Self-Service 8.x products from external and internal threat, which addresses all Self-Service applications except Requisitions XML (though they do cover web requisitions).
Architecture
Lawson self-service products (SEA) are accessed by users via a web browser. Most organizations have users accessing SEA with IE 6.0. SEA code is based on HTML and JavaScript with occasional CGI and servlet calls.
On UNIX, Lawson supports two types of IOS installations – “local”, where there is one set of CGI programs, and “remote”, where there are two sets of CGI programs – “real” ones that access Lawson daemons, and “stubs” that call “real” programs. “Remote” installation with both sets of CGI programs located on the same server (in two different directories) is usually called “loopback” installation.
Lawson has two main methods to access data – CGI calls and servlet calls. Web servers forward servlet calls to Tomcat or Websphere (servlet container application), that, in turn, calls RMI “listener” (a Java program), which accesses Lawson via a daemon. So, the servlet method of accessing Lawson data is always “remote”, though it can be set in a “loopback” configuration.
Lawson provides good protection from inside and outside threats, with the help of your operating system and web server software, though complex setup and configuration process may be needed. “Local” configuration may result in lesser security, because the Lawson application logic is running on the same physical server as the web server processes. So, I will only review the remote non-loopback configuration, where web server and Lawson application are located on two different physical servers.
Here is a diagram of data flow:
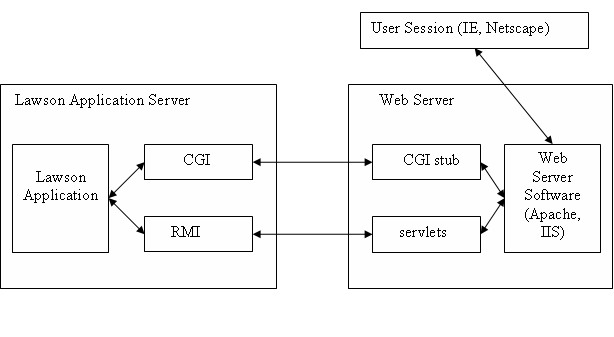
Most installations secure only the link between a User Session and Web server. While it is the most important step, as it protects the installation from outside hackers, securing CGI and servlet-to-RMI links is necessary to achieve high security.
Securing User Sessions
In this section we will review security of the data flowing between User Session and Web Server. There are several scenarios of potential compromise:
- An outside user gains access to Lawson web site via a “brute force” attack (gets valid name/password)
- An outside user gains access to Lawson web site via a flaw in a web server software<
- A valid lawson user gains “extra” privileges (can access items he/she not suppose to access)
- A session of a valid Lawson user is captured and misused by an inside (employee) or outside user (hacker)
Since “remote” installation does not access RDBMS that stores Lawson data directly, any compromise will not automatically give an intruder access to data. ESS/MSS does not have any files with hardcoded passwords, though a default username can be found in configuration files. In order to access and/or modify data, an intruder would have to have extensive knowledge of Lawson technology and internal workings. Hence, separation of web server and Lawson application server in a “remote” installation provides the first barrier to an intruder, both internal (the one accessing Lawson via corporate network where web server is located; usually – an employee), and external one.
Web Server security is a complex subject, and it’s vendor-specific. So, we will concentrate on only two aspects of web server security – SSL and process privileges.
Secure Socket Layer (SSL) protocol provides a means to establish an encrypted tunnel between the client (browser) and a web server. Once the tunnel is established, all communication between the client and the server will be encrypted. In order to eliminate “man in a middle” attack (scenario #4 above – an intruder captures user session and misuses captured information), SSL certificate signed by a trusted authority, such as Verisign, may be put on the server. Lawson SEA applications are fully SSL-compatible in the current versions.
All Lawson-related components do not need administrator privileges to operate. Web server and servlet container (Tomcat) may work under non-root account in UNIX. By restricting web server user and applying hardening procedures to the operating system and files you will essentially limit potential damage in case of a web server compromise that allows an intruder to access operating system files.
In my experience SSL certificates are only used to secure the link between a browser and a web server. Information between CGI stub and CGI, as well as information between servlets and RMI, is not encrypted. While SSL might be used for Java calls there, I have not tested such setup, and CGI stub-to-CGI calls cannot be encrypted this way. So, a different security mechanism should be provided to secure that channel.
Attack in a scenario #1 (brute force password guessing) can be prevented by putting password lockout in place. With IIS it can be done via Windows means (since IIS uses Windows users). Apache does not provide this function in a default configuration, but changing authentication mechanism to LDAP or custom scripting will accomplish this task.
Scenario #2 assumes an un-patched bug in a web server or Lawson software. I recommend subscribing to a security mailing list related to your web server software as well as Lawson update e-mails for Environment, IOS and Portal products, and apply security patches on a regular basis, after they have been tested. Note that gaining access via a flaw will not tell the intruder how to exploit data in Lawson. So, extensive knowledge of Lawson internal working would be required to get further access. In order to prevent configuration modifications that may cause the system to capture names and passwords, and propagate that information to an intruder, I recommend implementing file content change detection software, such as Tripwire as well as active intrusion detection systems, such as Snort. Most files and services on the web server are static, so most unplanned changes in Lawson-related directories, except the one that stores profiles in XML format, may indicate an “unusual” event. To better secure Lawson, put a web server on a DMZ, and separate it from Lawson application server with a firewall that has only certain ports open, two for servlet-to-RMI method (the second one is used in Reflux servlet, for example), and one for CGI stub-to-CGI access.
Scenario #3 – privileges gain - is the most cumbersome to address. High security there may require measures that will make security maintenance very time-consuming. We will not discuss Portal security here – it has enough material for another article. The only Portal form-related issue I’d like to address – RD30 should be made “read-only” for SEA users. This can be accomplished via LAUA security. Other forms may need to be secured as well. Extensive research may be needed to determine which forms to secure, and what access should remain.
In some SEA installations all SEA users point to the same LID account. While making user maintenance very simple, it also means that all users share the same security class in Lawson. That means by composing correct browser strings (which are very long – 100+ characters in many cases to do some meaningful query or change) one may inquire on someone else’s information, or change it under some circumstances. To provide high security each SEA user should have corresponding LID user with appropriate separate security class. However, that makes security very cumbersome to maintain. The potential compromise there would require a user that has comprehensive knowledge of Lawson CGI programs (or servlets) and their parameters. So, most companies do not apply such “extreme” security measures. Such misuse of SEA can be easily detected by log analysis on a web server, and can only be accomplished by a valid user (most probably an employee), so it not considered a significant threat. Misuse of Employee and Manager SEA can be prevented further by placing correct HR09/HR10 security in Lawson product line.
RD30 form has a field called “Access” that allows further security customization. It must be set to “Y” for all service centers except “Employee/Manager” one, where it must be set to “N” (see KB 521946). If it’s set to “Y”, LAUA validates security against security class. In Employee/Manager self-service access is controlled by the application itself per Employee Number listed in RD30 form. Because of that Lawson requires you to have a separate web user record for Employee/Manager self-service. Further information about LAUA security and its relation to self-service products is listed in KB 166200.
If users use Portal to login to SEA, required content can be used to remove “extra” features, such as ability to call forms by name (remove the search bar), switch product lines, use shortcuts, view and run jobs and reports, etc. While Lawson does not support those features, Knowledge Base lists them in “do at your own risk” fashion. I have successfully implemented all of the described features in various self-service implementations. Required content can also be used to propagate required menus to users without them going through the manual subscription process.
Securing data flow between Web and Lawson Application servers
Lawson application server does not need to be accessible by either internal or external SEA users directly on any port, so it can be located on a separate network. This will also prevent an employee from capturing a session between web server and a Lawson application server. Some network equipment, such as switches, may be used to achieve the same effect. While I did not test such configuration, it may also be possible to use encrypted SSH tunnel to provide communication security for data going between a web server and Lawson application server.
|
|
|
| |
|
|
|
| |
2. CUE 06: Was "9 on Your Mind"? |
 |
|
| |
|
|
|
| |
Even though I didn’t attend Lawson CUE this year in Orlando, I did get a number of eyewitness reports. I also viewed webcasts of the keynotes and listened in on a couple of the executive briefings.
CUE ’06 officially got off to a rousing (and loud!) early start thanks to a marching drum corps. What exactly was the message Lawson was trying to convey--perhaps that they march to a different drummer? It was all too Orwellian and reminiscent of Apple's 1984 ad.
Then it was on to CEO Harry Debes. Harry is a no-nonsense executive who has obviously been very successful thus far in re-focusing and re-energizing Lawson. His theme was “Matching Reality to the Promise” or conversely, “Turning promises into reality.” Part of that promise is that Lawson will never manage the company based on its share price. Harry showed a video featuring “Crazee Eddie” who was trying to sell Ginzu knives as well ERP software. I found it annoying and somewhat embarrassing.
Harry’s overall message was pretty vanilla, and if you've been paying attention there really wasn't a lot of new material except for a few highlights:
- The debut of the new “Lawson Community” message board
- A fleeting mention about Lawson's plans to start providing a hosting solution
- Some new support options, including an interesting one in which Lawson will “own” the maintenance of your customizations
- And, oh yeah, that new Lawson logo
Regardless, Harry got the job done and--more on this in a moment--actually showed some moments of levity the next day. He then brought Richard Lawson out for a brief update on Landmark.
Featured keynote speaker Malcolm Gladwell was next up, recounting stories from his books, Blink and The Tipping Point. If you’ve read the books, you know the stories, but it was still an engaging and entertaining talk.
Dean Hager started his Tuesday keynote with his usual showmanship and self-deprecating humor. In a video portraying his obsession with bettering Lawson's technology, we saw Dean in action. This included his ice fishing adventures (he even found a way to work his wife and three daughters into the story!), culminating in his "vision" of "9 on your mind" and the five reasons why it should be on your mind:
- Great application functionality
- New BI features
- Delivers on the promise of technology excellence
- Delivers improved support to you
- Path for the future
Following the video, Dean's message included in-person testimonials from beta clients of LSF 9.0 and the first Landmark app, Strategic Sourcing. Dean's keynote concluded with a cameo appearance by Lawson old-timer Matthew Allbee, who--using LID--raced against Dean--who was using Portal 9.0--in a test of application productivity. What it clearly demonstrated was that Portal, like Lawson, has finally come of age!
Following Dean’s keynote, Harry Debes came out to explain that the next speaker was a no-show after having a bout with food poisoning (which also afflicted my frequent LawsonGuru Letter contributor Keri White, who ended up missing most of CUE!) Debes then proceeded to warn the audience that he was forbade by Lawson's PR folks from telling jokes to kill some time. This--of course--was exactly what he proceeded to do!
It was an anxious and what could have been an embarrassing moment for Lawson, and clearly some of the audience wasn’t sure how to react. It showed a human side of Harry Debes that I don't think many of us had seen before. Now, perhaps if Lawson had allowed me to attend, they could have called me in to pass the time! Dean, I know you're reading this...whaddya think?
The Tuesday night entertainment was Chicago, which wowed the crowd with old favorites as well as new material. In a "7 degrees of Kevin Bacon" way, I felt like I WAS there. See, a friend of one of my college dorm-mates now plays guitar for them...
So, what were the key takeaways from CUE?
- While Landmark looks like it may be the real deal, it sounds like it is still living in the ivory tower and hasn't yet been exposed to many people. As soon as that happens and the defects start to surface...then we'll know more. Ever the skeptic, I'm starting to worry about it. The people behind it are so starry-eyed, it's scary. There was an interesting question on one of the conference calls, the gist of which was "if this is so great how come nobody was able to invent before? There is no silver bullet, no free lunch...".
- The user response to the Lawson Community forums will be interesting. I'm curious to see how well they do and what impact they have on the LawsonGuru.com forums and topica listserves.
- Lawson’s products continue to show maturity not only in the technology area, but in both the presentation layer and the application business logic as well. The new portal is vastly improved. The new Security and BI integration are what you'd expect from your ERP vendor. And the application enhancements continue to improve the core products.
- Vendor/exhibitor participation at CUE was remarkably decreased.
- The dual logistics of hosting the show at the Marriott World Center & Caribe Royale didn't go over well.
- I found the lack of enthusiasm during the keynotes embarrassing for Lawson. There were several times when there should have been applause, but the audience was nearly silent—notably during the unveiling of Lawson’s new logo.
To wrap up, my advice for those attending CUE is to not drink too much of the Kool-Aid, and remember that this is Lawson's show. Even so, here are a couple of customer comments that sum it up:
- "After attending CUE for nearly 10 years, I was (finally) very impressed. The show itself was well attended. Chicago played their hit songs and were a smash hit. The crowd was thoroughly satisfied."
- "This is my 5th CUE, and it was the best yet. Our CIO was in the executive sessions and was very impressed - as a result, we will be making a rather large (for us) investment in our Lawson systems."
After all is said and done, this is exactly what Lawson wants to hear! |
|
|
| |
|
|
|
| |
3. Worthwhile Reading |
 |
|
| |
|
|
|
| |
The People Who Count
- QUOTE OF THE ISSUE –
“The best way to have a good idea is to have a lot of ideas.”
-- Linus Pauling
With too few accountants to go around, companies are grabbing people wherever they can find them.
CFO Magazine, April 2006
http://www.cfo.com/article.cfm/5674536/c_5676923
What Happened to Do No Harm?
The Bush Administration’s ambitious effort to connect millions of electronic health records via a national network poses major risks.
CIO Magazine, April 1, 2006
http://www.cio.com/archive/040106/keynote.html
Software as a service: The next big thing
Applications are evolving in a Web ecosystem. Will enterprises one day get their key applications through the Web?
Infoworld, March 20 2006
http://www.infoworld.com/article/06/03/20/76103_12FEsaas_1.html
Captain Contingency
MIT logistics expert Yossi Sheffi talks with CIO about what companies can do to recover quickly from almost any type of disaster.
CIO Magazine, March 1, 2006
http://www.cio.com/archive/030106/sheffi.html
|
|
|
| |
|
|
|
| |
4. Lawson Tips & Tricks |
 |
|
| |
|
|
|
| |
Share your tips. Send them to mailto:letter-tips@lawsonguru.com.
You can view Tips & Tricks from past issues on the Tips & Tricks page on LawsonGuru.com
Which filename is that?
One of the questions I answer quite often is: "I know that the Lawson table prefix is GLT, but which table that is that?"
For example, you may want to use the Lawson Excel Query wizard to download Journal Entries which you have entered on GL40. You know that you can press Ctrl-Shift-O when you on any field in Lawson Portal, and the information about the field will be displayed in the browser Status Bar:
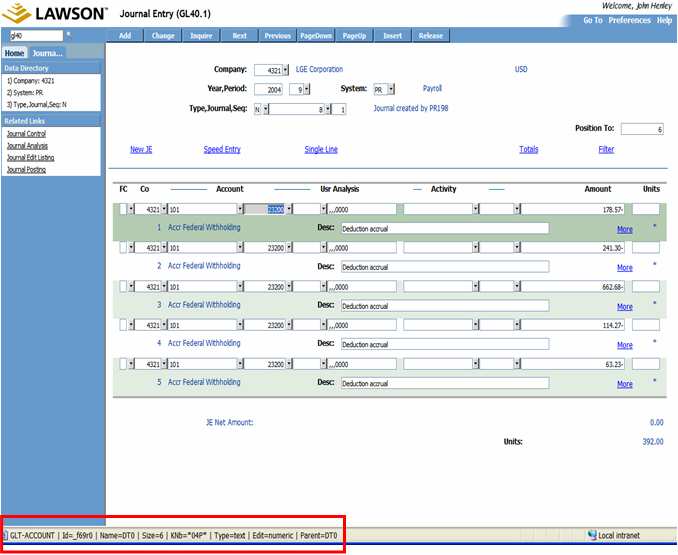
Lawson's table naming conventions are a 3-character prefix for every table, and often you'll only know the prefix. In this instance, the field name is GLT-ACCOUNT, which means that this is stored in the Lawson table with a prefix of GLT, but which table is that?
One quick way, which I use quite often with my clients, is to show them how to use the Lawson IOS DME service to retrieve a list of a product line's file names and abbreviations (adding the &OUT=export parameter to the URL will open it into Excel):
http://<webserver>/cgi-lawson/dme.exe?PROD=GEN&FILE=FILEDEF&FIELD=FILENAME;SYSTEMCODE;PREFIX&SELECT=PRODUCTLINE=<productline>&OUT=export
You can then save this in Excel, sort the list by abbreviation and keep it handy.
Here's another way you can look up the file abbreviations using the Lawson Query Wizard. If you have a recent version of the Query Wizard, you may have noticed that Lawson has added this lookup capability right on the field selection tab:
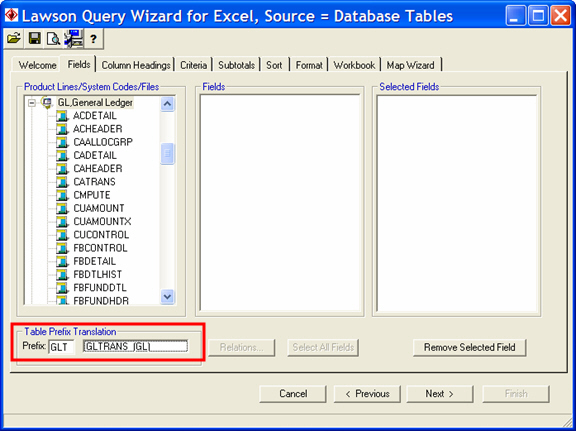
Enter the prefix, then press Tab and the table name and System Code will be displayed.
|
|
|
| |
|
|
|
| |
© Copyright 2006, Decision Analytics. All rights reserved. |
|
|
|
| Please share The LawsonGuru Letter in whole or in part as long as copyright and attribution are always included. |
| |
|
Decision Analytics is an independent consultancy, focusing on Lawson technical projects, and specializing in reporting, customization/modification, data conversion, and integration/interfaces. Please visit https://www.danalytics.com for more information.
|
| |
|